Preparing for CMMC Readiness Assessment: What You Need to Know
The Department of Defense (DoD) has been emphasizing for years the importance for contractors to protect Controlled Unclassified Information (CUI). Unfortunately, these efforts have not been successful, as a 2017 audit revealed that barely 60% of the Defense Industrial Base (DIB) were compliant with DFARS clause 252.204-7012. This is why organizations will soon have to gain the Cybersecurity Maturity Model Certification (CMMC) before being able to bid on new DoD contracts.
To assist organizations in gaining CMMC certification, we provide a readiness assessment that provides an organization with everything they need to become compliant. We help organizations understand what the controls in the CMMC model is looking for by digging into each assessment objective. This ensures organizations are equipped to handle controlled unclassified information before contract award, and be able to flow this requirement down throughout their entire supply chain.
At the end of our assessment, we create a System Security Plan (SSP) based upon the current CMMC requirements. This is one of three deliverables we provide with the other two being an SPRS score, and a Plan of Action and Milestones (POAM) to remediate any gaps. These 3 items ensure your business abides by the current requirements before CMMC is rolled out, while also protecting national security interests.
Short Summary
- CMMC Readiness Assessment is necessary for members of the defense industrial base to understand what they need to do to meet the compliance requirements.
- Organizations must evaluate existing cybersecurity controls, perform a mock CMMC audit and address any gaps to ensure compliance with security controls.
- Leveraging expert assistance can help organizations understand the complexities of CMMC readiness, develop an effective SSP that aligns with requirements and maintain ongoing compliance.
- Utilizing additional resources for your assessment like a Registered Provider Organization led by a qualified security assessor gives you increased assurance of certification readiness.
- The National Institute of Standards and Technology created NIST 800-171 to protect Department of Defense, and other federal government data.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The DoD has introduced the Cybersecurity Maturity Model Certification program to ensure the defense industrial base is able to adequately protect Federal Contract Information (FCI) and CUI data. DoD contractors have Defense Federal Acquisition Regulation Supplement (DFARS) clauses in their contracts that they are contractually obligated to comply with. The main clauses DoD contractors need to be aware of are:
- DFARS 7012- requires contractors to implement the 110 controls found in NIST SP 800 171
- DFARS 7019- contractors must upload their SPRS score, which is a self-assessment of the NIST 800-171 controls.
- DFARS 7020- the DoD can randomly audit contractors at any time to assess their compliance with NIST 800-171
- DFARS 7021-Contractors must pass a third party audit to ensure they have fully implemented NIST 800-171 to gain the Cybersecurity Maturity Model Certification. This is still undergoing the rulemaking process, and expected to be in contracts by 2024.
CMMC 2.0: Key Changes and Implications
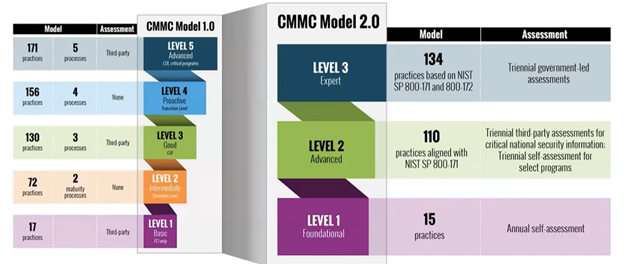
There have been two versions of the Cybersecurity Maturity Model Certification, versions 1.0 and CMMC 2.0. There were previously 5 CMMC Levels in version 1.0, but that has been reduced to 3 CMMC Levels in CMMC 2.0. This ensures organizations receive a comprehensive approach to compliance when handling federal contract information or CUI data. NIST SP 800-171 R2 was used as an alignment for CMMC Level 2 in order to simplify the assessment procedure and make it more accessible for organizations looking to make sure the CMMC model requirements have been fully implemented before contract award.
The required level companies must attain depend upon what type of controlled unclassified information they are managing. So understanding the required CMMC level can greatly aid their journey of ensuring the practices have been fully implemented and reduce the cost for companies to prepare their environment for assessment.
CMMC 2.0 Levels
CMMC Level 1 is for companies that only handle FCI. This maturity level requires a company to implement the 15 practices found in FAR 52.204-21, and they must perform an annual self assessment. These practices are considered, “basic cyber hygiene” that every organization should be doing.
CMMC Level 2 is for companies that handle CUI data. This maturity level requires a company that stores, processes or transmits CUI or other relevant defense information to pass an audit by a Certified Third Party Assessment Organization (C3PAO). C3PAO’s are authorized to give out the CMMC certification by the Cyber Accreditation Body (Cyber AB also known as the CMMC AB). The Cyber AB is responsible for the entire CMMC ecosystem.
CMMC Level 3 is for companies that process advanced CUI data critical to national security. This maturity level requires implementation of additional controls found in NIST 800-172 to prepare a company for Advanced Persistent Threats (APTs).
Understanding CMMC Readiness Assessment
These CMMC assessments are critical for a business to meet the cybersecurity mandates and continue working on DoD contracts. The CMMC Framework applies to both Federal Contract Information (FCI) and CUI data, requiring that practices be implemented, assessed for effectiveness, and potentially verified by a third party auditor when securing DOD contracts.
Navigating the complexities of the CMMC framework can present its challenges, but understanding the CMMC 2.0 levels will help ensure full implementation of the required CMMC level practices.
Steps to Conduct a Comprehensive CMMC Readiness Assessment
Organizations should go through a readiness assessment to ensure they are compliant with the required CMMC level. This three-step process includes evaluating existing security practices, conducting a practice audit, and addressing any identified weaknesses in order to strengthen their security posture. Through comprehensive analysis of their current environment, DoD contractors can gain an understanding of the effectiveness of established policies and identify potential flaws in them.
The following sections will provide guidance on analyzing these systems appropriately, performing mock audits efficiently, and dealing with discovered issues so that companies can be ready for official certification assessments from a C3PAO upon completion.
Evaluating Current Cybersecurity Controls
Organizations should assess their current cybersecurity practices in order to keep information assets safe, and make sure the appropriate security measures are correctly implemented. Evaluation of existing protections is essential for organizations when preparing for a CMMC assessment, as it allows them to identify potential vulnerabilities and ensure they have adequate protection standards that meet the NIST requirements.
Performing a Mock CMMC Audit
Organizations preparing for a CMMC assessment should conduct mock audits to evaluate the current state of their security systems and assess the various practices and controls according to their required CMMC level. This comprehensive process enables them to identify any gaps or weaknesses in cybersecurity measures which can then be addressed ahead of an official evaluation.
Crucially, it provides valuable feedback that allows organizations insight into how they can improve upon existing procedures and enhance their overall cyber protection capabilities. By adhering closely to these steps, companies will gain confidence in readiness for formal assessments next year.
Addressing Identified Gaps and Enhancing Security Posture
Assessing the existing security posture, identifying potential weaknesses, and creating a plan to address them, are essential steps in helping organizations improve their cybersecurity. This is significant for preventing data breaches and other cyber-attacks as well as making certain that CMMC 2.0 requirements are met.
Organizations should continuously review their security measures with specialist support available to ensure they remain compliant with all necessary CMMC 2.0 practices. This kind of continual improvement strategy can assist in ensuring secure and compliant operations at all times.
Preparing Your SSP for CMMC Assessment
An SSP is of vital importance for a CMMC assessment, as it outlines the security practices implemented to defend an organization’s information systems and data. It presents security assessors with an all-encompassing look at the company’s cybersecurity state. By building a well structured SSP, corporations can guarantee that any reviews undertaken run seamlessly while effectively demonstrating they meet the CMMC criteria.
Key Components of an Effective SSP
Organizations need to ensure a successful CMMC assessment by having an effective SSP in place. This requires making sure that all key components are included, such as risk assessments, policies and procedures, technical practices for implementation purposes, and documentation detailing these actions.
Training staff on cybersecurity protocols must be provided so they understand how their behavior is essential for ensuring top-level safety standards when dealing with confidential information. To demonstrate true commitment towards safeguarding valuable assets from digital threats, a comprehensive inventory of resources needs to exist, alongside established measures like physical protections and emergency response plans.
Aligning Your SSP with CMMC Requirements
It is essential for organizations to align their SSP with the CMMC requirements, as this guarantees that all security controls will adhere to DoD standards and help them pass a CMMC assessment. To be compliant during an evaluation process, those businesses must show they have taken steps to adequately implement these practices. By understanding the distinctions between each CMMC level, firms can ensure full compliance while maintaining their DoD contracts.
Leveraging Expert Assistance for CMMC Readiness
The importance of hiring the correct CMMC 2.0 compliance partner and forming a productive relationship is paramount when it comes to assessing an organization’s readiness. Such expert guidance can provide tremendous insight during this process while also helping organizations keep up with continuous changes in compliance requirements.
By leveraging professional support, businesses have more opportunities to identify areas of opportunity where their cybersecurity posture could be strengthened. This ensures that they are adequately prepared for all aspects of the assessment. Partnering with a capable provider and continuing collaboration will allow companies not only pass any given audit, but maintain overall CMMC 2.0 compliance going forward.
Selecting the Right CMMC Compliance Partner
Organizations can benefit greatly from selecting the right CMMC 2.0 compliance partner as they are able to provide assistance in achieving a company’s goals of becoming compliant. Prior to partnering with any firm, organizations should examine their expertise level, experience within the field of CMMC requirements, and perform a cost analysis.
Firms like FirstCall Consulting offer comprehensive advisory services which will prepare companies ahead of their audits and maintain their compliant status through on-going efforts. Through collaborating effectively with an experienced partner, you can be sure of a successful compliance program.

“We have been working with FirstCall Consulting for the past 6 years and they have been instrumental in our SAP projects and ongoing support. Their expertise and industry knowledge have helped us stabilize our environment and align our business processes with SAP’s capabilities. Thanks to their guidance, we have been able to maximize our use of SAP and reduce our support costs by over 60%. We highly recommend FirstCall Consulting as a valued business partner in the SAP Support and Managed Services space.”
Al Furman, Director of IT, Madden Communications, Inc.
Contact Us for More Information on Our Services
We’re eager to hear from you. Contact us today to learn more about our services and how we can customize them to your specific needs. Your journey towards improved operational efficiency and robust security starts with FirstCall.

