The security of both in-house operations and the supply chain tops the list of business executive’s responsibilities. In order to help with this sensitive issue, opt to work with vendors who are as dedicated to excellent protection measures as much as you are. This is one of the most important and effective ways to prevent cyber security issues that could harm your bottom line and future success.
When deciding what vendors to work with, choose only those with a strong track record of consistent and effective security. While it is important to remember that data breaches can happen to even the most dedicated organization, the frequency and severity of the issues tells you a lot about the vendor business. Lack of effective security measures makes it impossible for them to counter supply chain attacks.
If your vendors do not have strong security, nefarious threat actors could use their weakness to gain access to your systems and data.
This has been seen many times recently, here are the top 5 biggest supply chain attacks of 2022:
https://www.immuniweb.com/blog/5-biggest-supply-chain-attacks-in-2022-so-far.html
In the quest for high quality vendors you can count on, follow a regimented vetting process without fail. Do not cut corners or make allowances for any reason. If you discover any potential security risks, either address them directly or move on. This helps to ensure that you only work with product or service providers who are as committed to protecting the companies they work with as you are. The only question that remains is how you create a cyber supply chain vendor vetting process that gives you the information you need to make smart decisions.
Focus Tips for the Vendor Vetting Process
Take these topics into consideration when choosing vendors to work with.
1 – Security Strategy and Practices
Since security matters so much for your entire supply chain process and overall business success, dive into the details of every potential vendor’s system before signing any contracts. Have a clear conversation and insist on documentation so expectations are clear and met in case of any cyber threats. Some points to look for include regular scans for vulnerabilities, scheduled IT system updates, strict access authentication, and proper employee training protocols.
2 – Certifications and Regulatory Compliance
Different industries require specific legal certification and compliance with security regulations. Ensure the vendors you want to partner with are up to date and fully certified. This proves not only legality but also dedication to overall security strategy management. The upcoming CMMC requirements flows down the 3rd party audit requirement to any sub-contractor that handles CUI data. It is imperative that organizations get out ahead of this by either ensuring that their supply chain will become certified or find new vendors now that will.
3 – Where and How Do They Store Data?
Vendors will have access to your data and need to protect it as well as you do. How do they store it and what security protocols are in place? Options include on-site, off-site, or in the cloud. Your organization can determine which are acceptable for your own peace of mind. Again there are a number of compliance requirements organizations must consider. The commercial version of M365 is not compliant with CMMC, as CUI data must be held in a FedRamp High cloud environment:
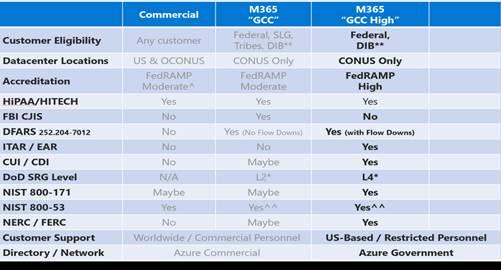
Organizations that handle CUI data have been migrating onto Microsoft GCC High to become CMMC compliant. However, GCC High is most of the time a 6 figure cost, and there are still additional requirements organizations must comply with.
That’s why FirstCall offers a solution that works on top of the commercial Microsoft and Google environments that does not require a cloud migration. Total costs are anywhere from 50 – 75% less than GCC High, and only users that handle CUI data need a license. Additionally, it helps comply with 102 out of the 110 NIST 800-171 requirements.
4 – How Do They Manage Data?
As important as data storage methods are, understanding what a vendor will do with your data if your companies are no longer affiliated is equally vital. Do you prefer full deletion, ongoing storage, or transfer to an agreed upon company? Other data management specifics matter too. These involve details about whether any fourth parties will have access to organization or customer data. Does the vendor company outsource?
5 – Business Continuity and Disaster Recovery (BCDR)
A BCDR outlines exactly what will happen if a cybersecurity threat manifests or a breach occurs. While recovering from an attack helps with future business operations and reputation, continuity is the critical part of the plan. Your company must continue to function smoothly with minimal interruptions in order to satisfy stakeholders and customers no matter what type of disaster occurs.
6 – Do They Have the Right Liability Insurance?
One essential part of a disaster recovery plan involves a full cyber liability insurance policy from a reputable provider. Globalization and digitalization have led to an increase in threats to IT systems and networks. If a data breach or other disaster occurs, the insurance coverage could protect both the vendor and your business from considerable losses. The vendors you choose must have a policy that compensates you for financial damages caused by a security breach.
Benefits of Working with a Skilled IT Services Team
While external IT teams will not choose vendors for you, FirstCall has the skills and expertise needed to help you navigate the process with Security requirements in mind. These necessary tasks involve extensive research, careful weighing of pros and cons, and full understanding of cyber supply chain issues. That is where FirstCall steps in.
Our goal is to minimize risks and create a holistic strategy that supports your vendor research and choice process. We assess possible points of vulnerability both in-house and associated with the third parties you collaborate with. This helps you choose only vendors who meet or exceed essential standards.
Contact us to get started with your cyber supply risk management consultation.