The Growing Intersection of DoD Funding and Cybersecurity
It’s no secret that Department of Defense contractors are facing more stringent cybersecurity requirements. However, most startups we talk to are surprised to find that DoD funding is increasingly dependent on the implementation of strong security measures, particularly for the protection of sensitive information. Compliance with NIST SP 800-171 is essential, and the Cybersecurity Maturity Model Certification (CMMC) is soon to be a prerequisite for contracts. SBIR/STTR award recipients must prioritize cybersecurity to not only secure funding but also safeguard innovative developments.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The Cybersecurity Maturity Model Certification (CMMC) is a framework developed by the Department of Defense (DoD) to standardize and verify the cybersecurity posture of organizations within the Defense Industrial Base (DIB). Its purpose is to safeguard Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) by ensuring that contractors implement and maintain adequate cybersecurity practices.
Historically, the Department of Defense relied on self-assessments to verify compliance with NIST SP 800-171, which outlines security program requirements for protecting CUI. However, this approach proved insufficient, as self-assessments lacked consistent implementation and independent verification. CMMC was introduced to address these shortcomings by establishing a tiered framework with independent third-party assessments. This ensures that organizations across the defense supply chain security, regardless of size or complexity, demonstrate a appropriate level of cybersecurity maturity commensurate with the sensitivity of the classified information they handle.
CMMC ensures cybersecurity compliance across the defense supply chain by requiring organizations to achieve specific appropriate levels based on the type of information they process. These levels encompass a range of cybersecurity practices and processes, from basic cyber hygiene to advanced threat protection. By mandating third-party assessments, CMMC provides a standardized and auditable mechanism for verifying that contractors have implemented the necessary security program controls. This reduces the risk of data breaches and strengthens the overall security posture of the DIB.
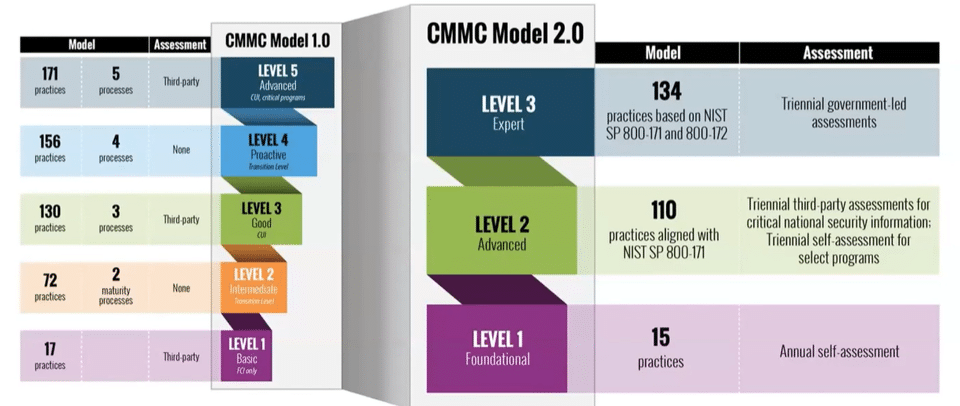
The framework has evolved significantly since its initial release. CMMC 2.0 represents a streamlined approach, reducing the number of maturity levels and simplifying compliance requirements. This evolution reflects the DoD’s commitment to balancing security practices with the practical needs of businesses, particularly small and medium-sized companies. By aligning CMMC with NIST SP 800-171 and focusing on the most critical security practices, CMMC 2.0 aims to enhance cybersecurity while minimizing the burden on DoD contractors.
CMMC Requirements for SBIR/STTR Awardees
The Cybersecurity Maturity Model Certification (CMMC) has become a non-negotiable requirement for small businesses and companies, particularly those receiving funding through the Small Business Innovation Research (SBIR) and Small Business Technology Transfer (STTR) programs. This mandate isn’t arbitrary; it reflects the Department of Defense’s critical need to safeguard sensitive information within its sprawling supply chain security, which increasingly relies on innovative small businesses and companies.
Why Small Businesses and Companies Receiving DoD Funding Must Comply with CMMC:
The Department of Defense’s decision to implement CMMC stems from a confluence of factors, all centered on protecting national security in an era of escalating cyber threats. Small businesses and companies, though agile and innovative, often lack the robust critical infrastructure of larger corporations, making them prime targets for malicious actors.
-
Protecting National Security Assets: Small Business Innovation Research and Small Business Technology Transfer (SBIR/STTR) projects often involve cutting-edge research and development, generating intellectual property and technical data that are vital to national defense. This information, classified as Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), must be rigorously protected.
-
Mitigating Supply Chain Vulnerabilities: Small businesses and companies are integral to the Department of Defense’s supply chain security, providing essential components, services, and technologies. A security breach at any point in this supply chain can have cascading effects, compromising the integrity of entire defense systems. CMMC aims to establish a baseline of cybersecurity maturity across the entire Defense Industrial Base (DIB).
-
Responding to Evolving Cyber Threats: Cyberattacks are becoming increasingly important, with adversaries employing advanced techniques to infiltrate networks and steal data. CMMC provides a standardized framework for implementing cybersecurity controls, ensuring that all DoD contractors, regardless of size, are equipped to defend against these threats.
-
Contractual Necessity: The DoD has made CMMC a contractual requirement, meaning that businesses or companies seeking to participate in Small Business Innovation Research and Small Business Technology Transfer (SBIR/STTR) programs must demonstrate compliance to be eligible for awards.
Key Cybersecurity Requirements for Handling Controlled Unclassified Information (CUI) and Federal Contract Information (FCI):
Understanding the distinction between Federal Contract Information and Controlled Unclassified Information is crucial.
-
Federal Contract Information (FCI): This refers to information provided by or generated for the federal government under a contract, but not intended for public release. Federal Contract Information requires basic safeguarding, primarily outlined in Federal Acquisition Regulation (FAR) clause 52.204-21, which emphasizes fundamental cyber hygiene.
-
Controlled Unclassified Information (CUI): This encompasses unclassified information that requires safeguarding due to its potential impact on national security. Controlled Unclassified Information is governed by NIST SP 800-171, which mandates the phased implementation of 110 specific security controls. These security controls cover a wide range of areas, including access control, incident response, and a system security plan.
Both Federal Contract Information and Controlled Unclassified Information necessitate core cybersecurity practices, including:
-
Access control: Limiting access to authorized personnel.
-
Security awareness training: Having a security team that educates employees on the best cybersecurity practices.
-
Incident response planning: Establishing procedures for handling security breaches.
-
System and network protection: Implementing firewalls, intrusion detection systems, and encryption.
Breakdown of CMMC Levels and What They Mean for Small Business Innovation Research and Small Business Technology Transfer (SBIR/STTR) Participants:
CMMC 2.0 simplifies the previous model, focusing on three key levels:
-
Level 1 (basic level): Foundational:
-
This level requires basic level cyber hygiene practices. It applies to businesses or companies handling FCI. Self-assessments are permitted within this level. For SBIR/STTR, this applies to projects with basic federal agency information.
-
-
Level 2: Advanced:
-
This level aligns with NIST SP 800-171, requiring advanced cybersecurity practices. It applies to businesses and companies handling CUI. Independent assessments by Certified Third-Party Assessment Organizations (C3PAOs) will be required for most acquisitions. Most SBIR/STTR projects that involve the handling of CUI will require at least this level of compliance.
-
-
Level 3: Expert:
-
This level focuses on protecting against advanced persistent threats (APTs). It applies to businesses and companies handling the most sensitive CUI. Federal Government-led assessments are required. This level will be for the highest priority DoD programs.
-
For SBIR/STTR awardees, understanding these levels is paramount.
-
Contract requirements: The required CMMC level will be specified in the contract.
-
Cost and time: Achieving higher levels requires significant investment from businesses and companies.
-
Competitive advantage: CMMC compliance enhances competitiveness.
-
Protecting intellectual property: A CMMC program helps safeguard valuable research and development data.
By proactively addressing CMMC requirements and compliance, SBIR/STTR awardees can not only secure Department of Defense funding, but also strengthen their overall cybersecurity posture, contributing to a more secure and resilient defense industrial base.
Steps to Achieve CMMC Compliance
Achieving CMMC compliance is a structured journey that requires careful planning and execution. It essentially breaks down into three core phases: assessment, phased implementation, and CMMC certification.
First, conducting a self-assessment and identifying security gaps is crucial. This involves a thorough review of your business or companies current cybersecurity posture against the specific CMMC level required. You’ll need to inventory your assets, examine existing security controls, security policies and procedures, and perform vulnerability scans to identify weaknesses. Comparing your current state to the requirements of NIST SP 800-171, which is the foundation for many CMMC levels, will reveal areas where your company falls short. This gap analysis allows you to prioritize and address the most critical vulnerabilities.
Second, implementing cybersecurity best practices and required controls involves taking the findings from your self-assessment and turning them into actionable steps. This includes developing a System Security Plan (SSP) that outlines your security practices, policies and procedures. You’ll need to implement technical controls, such as access controls, encryption, and firewalls, as well as administrative controls like security awareness training and incident response plans. Meticulous documentation is essential for demonstrating compliance. Consistent monitoring of these controls after phased implementation is also vital.
Finally, working with third-party assessors and preparing for CMMC certification is the culmination of your efforts. You’ll need to select a Certified Third-Party Assessment Organization (C3PAO) to conduct the official assessment. Working with the C3PAO to clearly define the assessment scope is necessary before gathering all the required evidence, such as policies, procedures, and system configurations. You may also consider a pre-assessment to identify any remaining gaps before the official audit. During the assessment, you’ll need to cooperate fully with the C3PAO and address any findings they raise. Upon successful completion, you’ll receive your CMMC certification, which needs to be maintained through ongoing compliance efforts.
Common Challenges Small Businesses and Companies Face with CMMC Compliance
1. Cost and Resource Constraints:
-
Financial Burden:
-
Implementing the necessary cybersecurity controls, purchasing required software and hardware, and undergoing assessments can be costly. Small businesses and companies often operate on tight budgets, making it difficult to allocate substantial funds to cybersecurity.
-
-
Limited Staffing:
-
Many small businesses and companies lack dedicated IT or cybersecurity personnel. Existing staff may have limited expertise in cybersecurity, making it challenging to implement and maintain required controls. The time required to implement and maintain a CMMC compliant system, takes away from other essential business functions.
-
• 2. Understanding Complex Cybersecurity Frameworks:
-
Technical Complexity:
-
NIST SP 800-171 and the CMMC program involve complex technical requirements that can be difficult for non-experts to understand. Interpreting and implementing these requirements can be overwhelming for small business and company owners who may lack specialized cybersecurity requirements.
-
-
Navigating Regulatory Language:
-
The language used in cybersecurity frameworks and regulations can be dense and difficult to decipher to those not used to it. Small businesses and companies may struggle to understand the specific cybersecurity requirements and how they apply to their operations.
-
• 3. Finding Qualified Cybersecurity Professionals or Managed Service Providers (MSPs):
-
Talent Shortage:
-
There’s a global shortage of cybersecurity professionals, making it difficult for small businesses and companies to find qualified personnel. Larger corporations often have the resources to attract and retain top talent that know the cybersecurity requirements, leaving small businesses and companies at a disadvantage.
-
-
MSPs and their availability:
-
While Managed Service Providers can be a solution, finding one that is both qualified in CMMC, and affordable, can be difficult. Many MSP’s are still learning the CMMC process themselves.
-
-
Cost of Expertise:
-
Hiring cybersecurity professionals or engaging MSPs can be expensive, adding to the financial burden for small businesses and companies. Even if a small business or company can afford an MSP, there is no guarantee that the MSP has the required knowledge.
-
In essence, small businesses and companies struggle with CMMC compliance due to a combination of financial limitations, technical complexity, and difficulties in securing qualified expertise.
Why CMMC Compliance Matters Beyond SBIR/STTR
CMMC compliance extends its significance far beyond the realm of SBIR/STTR projects, offering substantial and lasting advantages for any small business or company engaged with or aspiring to obtain a contract with the Department of Defense (DoD contract). Here’s why:
1. Long-Term Benefits of Cybersecurity Compliance for Business Growth:
-
Enhanced Business Reputation: A verified CMMC certification signals to potential clients, partners, and stakeholders that your organization prioritizes cybersecurity. This builds trust and credibility, which can translate into increased business opportunities.
-
Competitive Advantage: In an increasingly digital world, cybersecurity is a critical differentiator. Businesses demonstrating robust cybersecurity practices are more attractive to customers and partners concerned about data protection.
-
Operational Resilience: Implementing strong cybersecurity controls reduces the risk of costly data breaches, system downtime, and reputational damage. This enhances operational resilience and ensures business continuity.
-
Increased Efficiency: Streamlining cybersecurity processes often leads to improved overall IT management and efficiency, benefiting various aspects of your business.
2. Expanding Eligibility for More DoD Contracts and Subcontracting Opportunities:
-
Broader DoD Contract Access: CMMC compliance opens doors to a wider range of DoD contracts, including those involving sensitive information beyond SBIR/STTR projects.
-
Subcontracting Opportunities: Prime contractors are increasingly requiring their subcontractors to be in CMMC compliance. This means that businesses with CMMC certification are more likely to be selected as subcontractors on major DoD projects.
-
Future-Proofing Your Business: As the DoD continues to prioritize cybersecurity and security programs, CMMC compliance will become a standard requirement for most, if not all, DoD contracts. Being proactive ensures your business remains competitive and eligible for future opportunities.
3. Improving Overall Data Protection and Reducing Cyber Threats:
-
Protecting Intellectual Property: CMMC compliance helps safeguard valuable intellectual property, trade secrets, and proprietary information from cyber threats.
-
Safeguarding Customer Data: Implementing strong cybersecurity controls protects sensitive customer data, enhancing customer trust and loyalty.
-
Mitigating Cyber Risks: CMMC compliance reduces the likelihood and impact of cyberattacks, minimizing financial losses, operational disruptions, and reputational damage.
-
Enhancing National Security: By strengthening the cybersecurity of the entire defense industrial base, CMMC compliance contributes to the overall security of the nation.
In essence, CMMC compliance is not just a regulatory obligation but a strategic investment that yields long-term benefits, expands business opportunities, and enhances overall cybersecurity posture. It’s a key component of building a sustainable and secure business in the modern defense landscape.
How to Get Started with CMMC for Your DoD-Funded Project
Getting started with CMMC for your DoD-funded project can seem daunting, but there are actionable steps and resources available to small businesses and companies. Here’s a practical guide:
1. Leverage Free and Low-Cost Resources:
-
DoD’s Project Spectrum:
-
This platform provides a wealth of resources, including cybersecurity guides, templates, and tools specifically designed for small businesses and companies within the Defense Industrial Base (DIB). It often offers simplified explanations of the CMMC framework and program requirements. It can be a great place to start learning, and finding out what is required of your specific business.
-
-
NIST SP Resources:
-
The National Institute of Standards and Technology (NIST) offers a wealth of free resources, including NIST SP 800-171, which is the foundation for CMMC Level 2. NIST SP provides guides, publications, and tools to help organizations understand and implement cybersecurity controls that align with NIST SP standards. Their website is the official source for much of the information regarding CUI protection. Contractors working with the Department of Defense must comply with NIST SP 800-171 to protect controlled unclassified information from cybersecurity threats.
-
-
Small Business Administration (SBA):
-
The SBA provides resources and guidance to small businesses and companies on various topics, including cybersecurity. They may offer training programs or connect you with local resources.
-
2. Finding Cybersecurity Consultants and CMMC Training Programs:
-
Cybersecurity Consultants:
-
Seek consultants with experience in CMMC compliance and NIST SP 800-171. Look for consultants who understand the specific needs of small businesses and companies. Check for certified C3PAOs, or consultants that are working towards that CMMC certification.
-
-
CMMC Training Programs:
-
Look for training programs offered by reputable organizations, such as community colleges, universities, or industry associations. Ensure the training programs cover the specific CMMC level relevant to your business. Look for Registered Provider Organizations (RPOs) and Registered Practitioners (RPs) that can help guide you through the certification process.
-
-
Industry Associations:
-
Many industry associations offer cybersecurity resources and training programs to their members.
-
These associations can also provide networking opportunities with other businesses that have gone through the CMMC process. Knowing the CMMC framework will make these networking opportunities an optimal experience.
-
3. Integrating Cybersecurity into Business Operations:
-
Conduct a Gap Analysis:
-
Assess your current cybersecurity posture against the requirements of the relevant CMMC level and identify areas where your organization needs to improve its security controls.
-
-
Develop a System Security Plan (SSP):
-
In order to develop a system security plan, you need to document your organization’s cybersecurity policies, procedures, and controls. The SSP should clearly outline how your organization meets the requirements of the CMMC framework.
-
-
Implement Security Controls:
-
Implement the necessary security controls based on your gap analysis and SSP. This may involve implementing new technologies, updating existing systems, or developing new policies and procedures.
-
-
Document Everything:
-
Thorough documentation of implemented controls, policies, and procedures is vital for CMMC assessments.
-
-
Continuous Monitoring and Improvement:
-
Cybersecurity is an ongoing process. Regularly monitor your security controls and make adjustments as needed. Stay up-to-date on the latest cybersecurity threats and best practices.
-
By taking these steps, small businesses and companies can effectively navigate the CMMC process and build a strong cybersecurity foundation for future success in DoD contracting. This will also be key in protecting these businesses.
Conclusion: Preparing for a Cyber-Secure Future in DoD Contracting
In conclusion, preparing for a cyber-secure future in Department of Defense contracting is not just a regulatory hurdle, but a strategic imperative. For SBIR/STTR participants, CMMC compliance is no longer optional; it’s a fundamental requirement for participating in the defense industrial base. The need to protect sensitive information, defend against increasingly sophisticated cyber threats, and maintain the integrity of the DoD’s supply chain security necessitates a robust cybersecurity posture.
Therefore, it is strongly encouraged that small businesses involved in DoD contracting begin the CMMC compliance and certification process as early as possible. Proactive engagement allows for thorough gap analysis, adequate time for remediation, and the ability to navigate the complexities of the CMMC certification process. Delaying compliance can lead to missed contract opportunities, increased costs, and potential security breaches that could severely impact business operations and the nation’s security. The national institute increased funding for weapons systems to enhance their cybersecurity measures, protecting them from potential cyber threats and adversarial attacks.
Ultimately, cybersecurity plays a pivotal role in ensuring long-term success in defense contracting as well as protecting businesses. In an era where cyber threats are constantly evolving, demonstrating a commitment to cybersecurity is essential for building trust with the Department of Defense and establishing a competitive advantage. By investing in robust cybersecurity measures, small businesses not only protect sensitive information but also contribute to the overall resilience of the defense ecosystem, paving the way for sustained growth and success in the dynamic landscape of Department of Defense contracting.